procd: A Privacy-preserving Robust Implementation to Discover Contacts in Social Networks
Volltext
Abbildung
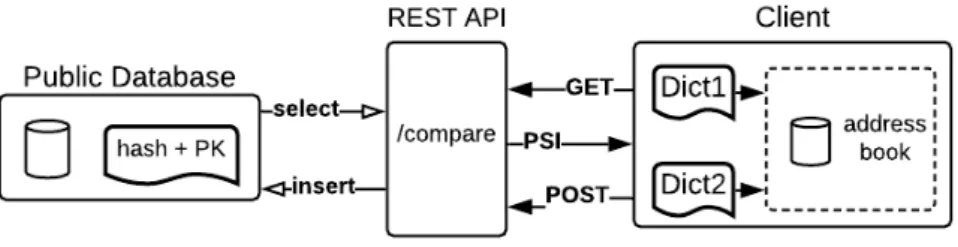
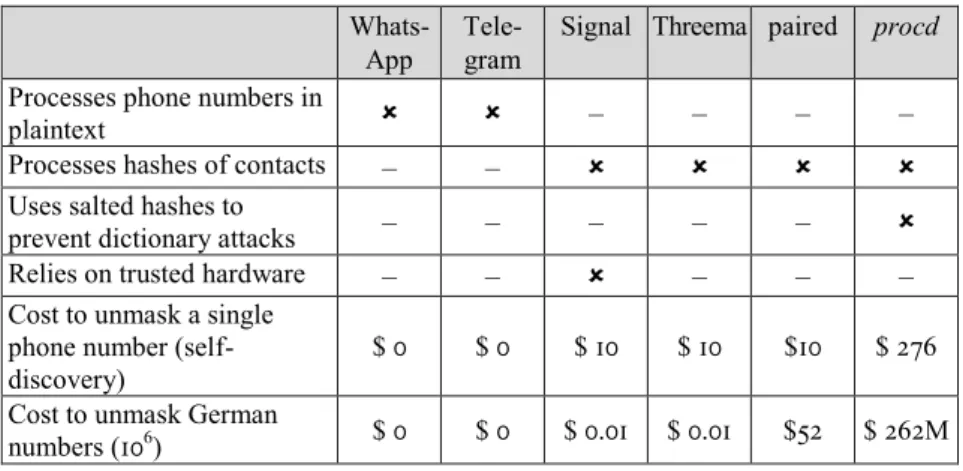
ÄHNLICHE DOKUMENTE
With regard to the discussion on environmental policy instruments (as well as on policy instruments in general) and the discussion amongst political scientists of state
In the end, we compared our results in the non-equilibrium case to experimental measure- ments of noise in quantum point contacts and, again, to theoretical predictions from
SIOC provides on the one hand a unified ontology to describe such online communities, and secondly, several exporters from that translate community information from weblogs, forums,
Second, to render migration a rational choice for an individual, we assume that the income in the destination country, Y, is sufficiently high to allow the individual
● Feature 4a (Sharing over time): I want to be able to quickly understand how much misinformation people have shared over time through an overall misinformation score.. ● Feature
After an overview of catastrophe insurance and its role for loss and damage from climate change (Sect. 21.2), the discussion turns to the benefits and costs of insurance (Sect.
Keywords: Autocatalysis, Ecological goal functions, Network analysis, Succession, Sustainability, Systems ecology, Thermodynamics.. 1 INTRODUCTION – A
Establishing marine protected areas could limit access to marine resources for food and nutrition security; however, fisheries and other natural resource uses generally benefit