Research Collection
Master Thesis
Modeling and Analysis of the SCION Dataplane in Tamarin
Author(s):
Frankovska, Zuzana Publication Date:
2021
Permanent Link:
https://doi.org/10.3929/ethz-b-000477332
Rights / License:
In Copyright - Non-Commercial Use Permitted
This page was generated automatically upon download from the ETH Zurich Research Collection. For more
information please consult the Terms of use.
of the SCION Dataplane in Tamarin
Master Thesis Zuzana Frankovsk´ a
25 th March, 2021
Professor: Prof. David Basin
Supervisors: Dr. Christoph Sprenger, Dr. Ralf Sasse, and Tobias Klenze
Department of Computer Science, ETH Z¨ urich
Abstract
The Internet we use today has not been designed to be as secure as we need it to be. New future Internet architectures, such as SCION, are being designed with stronger security demands. SCION includes a controlplane protocol for discov- ering the network topology and designating authorized paths, and a dataplane protocol for transferring data packets along authorized paths.
In this thesis, we study not only the initial dataplane protocol used in SCION, but also the protocol used in the SCION implementation by Anapaya, and the four protocols in the EPIC family, which can also be used in the SCION architec- ture. The analyzed security properties of these protocols are path authorization, packet authentication, source authentication, and path validation. By achieving these properties, the protocols can help in preventing various routing attacks and provide more control over the paths traversed by packets.
We analyze the security properties by symbolic modeling of the protocols and
automatic verification in the Tamarin tool. This gives us formal guarantees of
the security of the studied protocols. We are able to model the protocols for
an arbitrary network topology and an arbitrary set of authorized paths, but the
maximum length of authorized paths has to be limited. Furthermore, we create
an infrastructure that can be easily reused for analyzing more similar protocols
and properties in the future.
I want to thank my supervisors for spending a lot of time guiding me through this thesis and for all their feedback. Namely, I want to thank Christoph Sprenger for proposing the project and laying the foundation for my work, Ralf Sasse for his help with the peculiarities of Tamarin, and Tobias Klenze for being able to understand my models and always having many ideas.
I am thankful to Prof. David Basin for the opportunity to do this thesis in his
research group.
Contents
1 Introduction 1
1.1 Motivation . . . . 1
1.2 Contributions . . . . 2
1.3 Related Work . . . . 3
1.4 Outline . . . . 3
2 Background 4 2.1 SCION . . . . 4
2.1.1 SCION Controlplane . . . . 5
2.1.2 SCION Dataplane . . . . 6
2.1.3 Implementation by Anapaya . . . . 7
2.2 EPIC . . . . 8
2.2.1 Level 0 . . . . 8
2.2.2 Level 1 . . . . 8
2.2.3 Level 2 . . . . 9
2.2.4 Level 3 . . . . 10
2.3 Security Properties . . . . 11
2.4 Tamarin . . . . 12
2.4.1 Terms . . . . 12
2.4.2 Rules . . . . 13
2.4.3 Properties . . . . 15
2.4.4 Proof search . . . . 16
3 Attacker Model 18 3.1 Classic Dolev–Yao . . . . 18
3.2 Localized Dolev–Yao . . . . 19
4 Modeling Security Properties 22 4.1 Path authorization . . . . 22
4.2 Packet authentication . . . . 25
4.3 Source authentication . . . . 27
4.4 Path validation . . . . 27
5 SCION Dataplane Model 31
5.1 Infrastructure rules . . . . 31
5.2 Protocol rules . . . . 34
6 Anapaya Implementation model 39 7 EPIC protocol model 42 7.1 Level 0 . . . . 42
7.2 Level 1 . . . . 42
7.3 Level 2 . . . . 44
7.3.1 Localized Dolev–Yao . . . . 44
7.3.2 Classic Dolev–Yao . . . . 46
7.3.3 Protocol rules . . . . 46
7.4 Level 3 . . . . 48
8 Fixed Network Topology 50 8.1 Generating topologies . . . . 50
8.2 Generating authorized paths . . . . 51
8.3 Model with fixed topology . . . . 51
9 Experiments 54 9.1 Infrastructure . . . . 54
9.2 Speed improvements . . . . 54
9.3 Results . . . . 56
10 Conclusion 59 10.1 Discussion . . . . 59
Bibliography 61
Chapter 1
Introduction
1.1 Motivation
While the Internet is widely used for many different purposes today, it was not designed with such scale and versatility in mind. The underlying protocols are outdated and have many security vulnerabilities. The routing is based on the insecure Border Gateway Protocol.
The vulnerabilities have become a significant issue since today’s society heavily relies on the Internet, using it for banking, voting, and more. For some of them, there are existing solutions working on top of the old architecture, but they are constrained by the old design and often too slow to be used in practice. For others, such as distributed denial of service attack, there are no solutions without spending a large amount of resources, which not everyone can afford. The goal of the SCION project [1] is to completely redesign the infrastructure of the Internet from a clean slate, greatly improving security, privacy and trust, while retaining high efficiency. Currently, there already exists a working implementation of SCION by Anapaya [2].
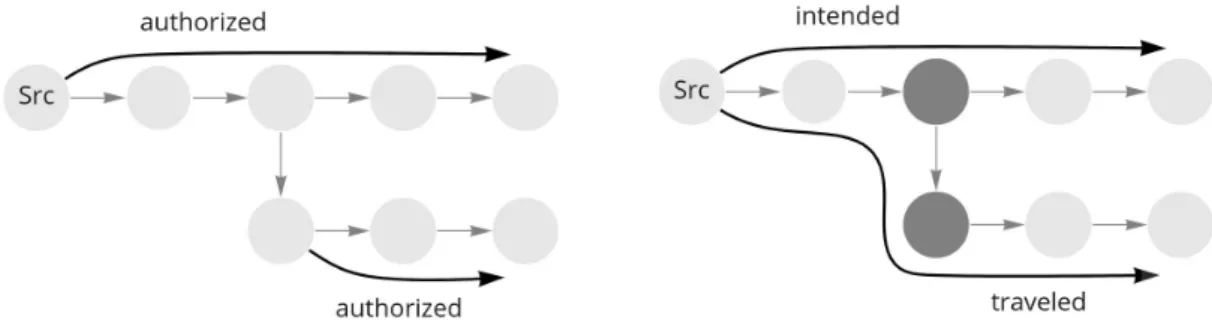
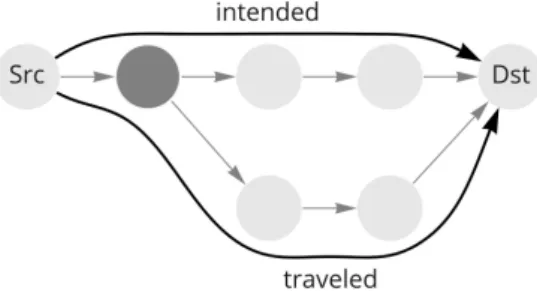
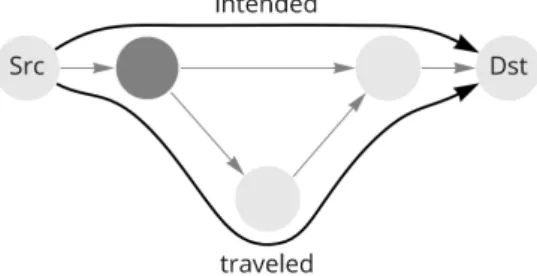
In the current Internet, there is little control over the paths that packets travel, and that leaves space for various routing attacks. One of the guarantees that SCION aims to provide is path authorization, which means that packets can travel only along paths that are authorized for them. This could prevent some of the routing attacks and enable new functionality of the net- work. Network operators can enforce routing policies, balance the amount of traffic between different routes to increase efficiency, or even offer different routes at different prices. Even stronger guarantees would be packet authentication, source authentication, and path validation, which are promised by the EPIC dataplane protocols [3] that can be used with the SCION architecture. Packet authentication prevents modifications of the packet. Source authentica- tion forbids spoofing the source address and thus provides accountability for each packet.
Path validation gives assurance about the traveled path to the source or the destination of the packet. Together, these security properties help to prevent many attacks that are nowadays very concerning, but also create possibilities for new ways how to make the Internet faster and fairer.
There are tools that can help to prove that these properties hold by automating parts of the
process. One such tool is Tamarin [4], which provides static automatic verification of symbolic
protocol models. Automatic verification can greatly speed up the proving process and pro-
vide formal guarantees and thus also greater credibility of the results. Additionally, once we
have specified a model in Tamarin for one protocol, it is easy to modify it for more similar
protocols and quickly verify the properties. Modeling the protocols in Tamarin introduces
a few challenges. To analyze the above-mentioned properties, we have to take into account that there can be arbitrarily many participants in a single protocol run, since each on-path AS is participating. Furthermore, we are not only interested in one authorized path, but how different paths, some of them authorized, can interact with each other. For example, we are interested in observing whether the adversary can combine two authorized paths to create a path that is not authorized, and send a packet along that path.
1.2 Contributions
The aim of this work is to model the SCION Dataplane protocol and multiple alternative protocols in Tamarin and analyze their security properties. Multiple variants of the protocol are modeled, namely:
• the initial design of the SCION dataplane protocol
• the protocol used in the implementation by Anapaya
• four levels of the EPIC protocols
The relevant security properties analyzed are path authorization, packet authentication, source authentication, and path validation. Path validation has two variants, defined for the destina- tion and for the source. The attacker model is a localized variant of the Dolev–Yao adversary for path authorization and the classic Dolev–Yao model for the rest.
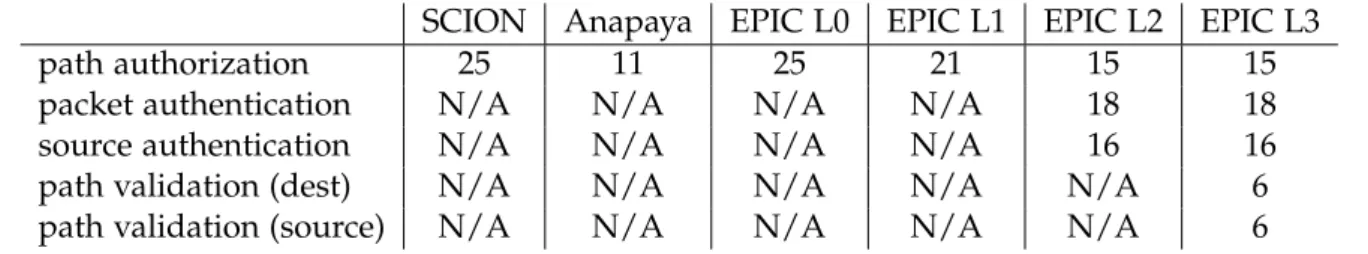
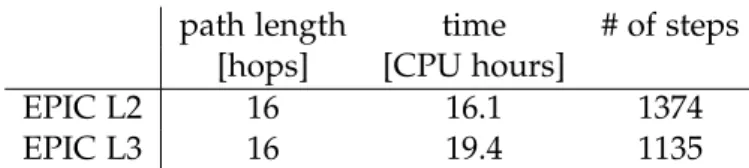
We describe the Tamarin models for each protocol and each attacker model. We show that these properties can be verified for an arbitrary topology and an arbitrary set of authorized paths, as long as we limit the maximum length of authorized paths. All the security prop- erties that are expected to be satisfied are indeed verified by Tamarin for an arbitrary set of authorized paths up to a given length. The verified properties and the maximum authorized path lengths are listed in Table 1.1. If the entry in the table is ’N/A’, it means that the given property is not supposed to hold for the given protocol, therefore it was not analyzed in this thesis.
SCION Anapaya EPIC L0 EPIC L1 EPIC L2 EPIC L3
path authorization 25 11 25 21 15 15
packet authentication N/A N/A N/A N/A 18 18
source authentication N/A N/A N/A N/A 16 16
path validation (dest) N/A N/A N/A N/A N/A 6
path validation (source) N/A N/A N/A N/A N/A 6
Table 1.1: Maximum length of authorized paths for which the listed security properties were verified for the listed protocols
We create a script that can generate a Tamarin theory file for a given maximum authorized
path length for a specified protocol model. Additionally, we can also generate Tamarin theory
files with fixed topologies. We create a script generating different fixed network topologies
with a fixed set of authorized paths, with options to specify parameters and various condi-
tions. These scripts are a part of an infrastructure for generating Tamarin theory files and
subsequently running Tamarin on the theory files. It can be reused for other similar protocols
in the future.
1.3. Related Work
1.3 Related Work
The studied dataplane protocols are described in the following works. The initial design of the SCION dataplane is described in the book ”SCION: A Secure Internet Architecture”
published in 2017 [1]. The protocol used in the implementation by Anapaya is described in the documentation on their website [2]. The EPIC protocols were introduced by Legner et al.
in 2020 [3]. The security properties of the SCION protocol and the EPIC protocols are argued theoretically in these works. We do not know of the existence of any security proofs for the Anapaya protocol used in the implementation. There are also other designs of dataplane protocols, such as ICING [5] or OPT [6], which we do not study.
Security properties of numerous network protocols have been verified by various tools for either automatic or interactive verification. Paulson [7] used Isabelle/HOL [8], a generic proof assistant performing interactive verification, to model network protocols and prove their security properties. Coq [9], another proof assistant, was used by Zhang et al. [10] to prove source authentication and path validation of OPT. Tamarin has been previously used successfully for verification of security properties of network protocols such as TLS 1.3 [11]
or 5G [12]. It has even been used on a different part of the SCION architecture, the hidden paths [13].
More closely related to this thesis, path authorization for the SCION dataplane protocol and the EPIC L1 and L2 protocols has been verified in Isabelle/HOL by Klenze et al. in 2021 [14]. The paper mentions that the authors anticipated that Tamarin can be used for path authorization only with a small fixed topology and a fixed set of authorized paths, which we have disproven. The advantages of using Tamarin instead of Isabelle/HOL are that it performs the proof automatically and it is tailored for the analysis of security protocols.
Another advantage of using Tamarin for modeling the Anapaya protocol is that it has a built- in message theory for exclusive-or [15]. However, while the proofs in Isabelle/HOL hold for an arbitrary topology with an arbitrary set of authorized paths, in our models in Tamarin, we have to limit the maximum length of authorized paths.
1.4 Outline
This thesis is structured as follows. Chapter 2 introduces the studied protocols, the analyzed
security properties, and the Tamarin tool. In Chapter 3, we describe the two attacker models
we use in our models. In Chapter 4, we describe how we model the security properties. In
Chapters 5, 6, and 7, we describe the models for the initial SCION dataplane protocol, the
protocol used in Anapaya’s implementation, and the EPIC protocols, respectively. In Chap-
ter 8, we discuss how we can generate random network topologies and sets of authorized
paths, and subsequently modify the models to use a fixed topology. In Chapter 9, we de-
scribe the conducted experiments and present their results. Chapter 10 discusses the results
and concludes the report.
Background
2.1 SCION
SCION is a clean-slate future Internet architecture designed to provide route control, failure isolation, and explicit trust information for end-to-end communication [1]. It aims to improve availability, transparency, control, efficiency, scalability, and flexible trust.
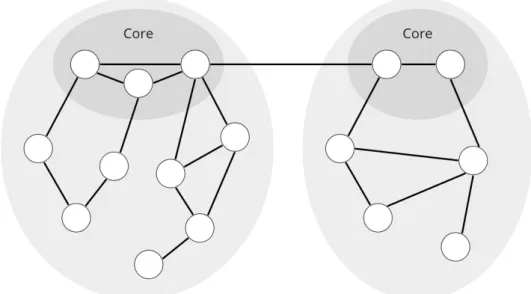
The Internet is organized into networks called autonomous systems (AS). In SCION, ASes are organized into groups of independent routing planes called isolation domains (ISD). This sepa- ration provides the possibility for each ISD to agree on individual policies, keys, and author- ities. Entities outside an ISD cannot affect routing within that ISD. Traffic is divided into two levels – inside of a domain and between domains. A subset of ASes in an isolation domain forms the core, and so they are the core ASes. They are the root of trust for the ISD, they have the responsibility of managing the ISD, and only they are linked to the other ISDs, so they facilitate inter-domain communication. You can see an example of two ISDs in Figure 2.1.
Each small white circle represents an AS. From now on, we will be focusing only on the intra-domain traffic for the sake of simplicity.
Figure 2.1: Example of isolation domains in SCION
2.1. SCION SCION networking protocols are composed of two parts: controlplane and dataplane. The controlplane is used for discovering the topology and path information. It authorizes path segments by which packets can travel. The dataplane is used for forwarding data transfer.
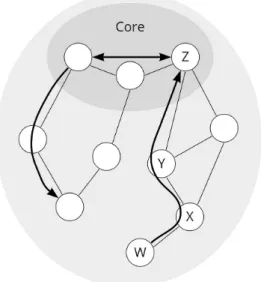
There are three types of path segments. A path segment from a non-core AS to the core is an up-segment, a path segment from the core to a non-core AS is a down-segment and a path segment between core ASes is a core-segment. Figure 2.2 shows examples of these types of segments. A path traveled by a packet can be comprised of one or multiple of these segments, but at most one of each. From now on, we will be focusing only on the up-segments.
Figure 2.2: Example of different types of path segments in SCION
2.1.1 SCION Controlplane
The controlplane is responsible for discovering and distributing authorized paths. It also ensures that these paths are acyclic and fulfill any potential additional policies. Inside the ISD, core ASes are periodically and asynchronously looking for paths to authorize. This is done by beaconing, i.e. sending path-segment construction beacons (PCBs) to flood the network in the downward direction. That is the opposite direction to the data transfer in up-segments.
Every AS has beacon servers that create and propagate PCBs and path servers that manage the registration and lookup of authorized paths.
While traversing the ISD, PCBs collect information about ASes. A PCB consists of an info field and an AS entry for all traversed ASes. Each AS entry is signed and stores, apart from other information, a hop entry, which stores the information about its interfaces and a hop field. The hop field is composed of hop information (H I) and hop authenticators σ. The dataplane security properties will be expressed in terms of the information contained in these hop fields.
Next, we will show how the σs are computed. Let us say that we want to authenticate the
segment W − X − Y − Z from Figure 2.2. A beacon server at the core AS Z creates a PCB. For
the first AS entry corresponding to the AS Z, it computes σ
Zas a MAC of its hop information
H I
Z. The secret key K
Zis used for this MAC. This key is also shared among the AS’s routers.
σ
Z= MAC
KZ( H I
Z) [[ 0 : l
v]]
The notation [[ 0 : l
v]] signifies truncating the byte string to the first l
vbytes. The MACs are truncated for efficiency reasons. As the PCB travels down the network, the subsequent ASes also compute their σs, but they include the σ and the H I of the previous AS in their MAC.
For example, σ
Yand σ
Xare computed as follows.
σ
Y= MAC
KY( H I
Y|| H I
Z|| σ
Z) [[ 0 : l
v]]
σ
X= MAC
KX( H I
X|| H I
Y|| σ
Y) [[ 0 : l
v]]
This process creates a nested authenticator of the path. The last AS is W and its σ will be equal to the following, if we omit the truncation.
σ
W= MAC
KW( H I
W|| H I
X||( MAC
KX( H I
X|| H I
Y||( MAC
KY( H I
Y|| H I
Z||( MAC
KZ( H I
Z))))) The hop information (H I) consists of an AS identifier, an ingress interface, and an egress in- terface. Each link going in or out of an AS has assigned a unique interface, thus each link between two neighboring ASes is uniquely identified by an ingress and an egress interface.
H I = IgIF || ID || EgIF
Once the PCB arrives at an AS, the AS can decide whether to authorize the path traveled by that PCB. This is decided and recorded by the path server. The path server turns the PCB into a path segment by signing it. An authorized segment is defined by a path description, which is a sequence of H Is, and a sequence of σs. This information is contained in hop fields.
Furthermore, each AS can decide whether or not to propagate the PCB forward.
2.1.2 SCION Dataplane
Once the authorized paths are established, the next step is data packet transfer. If an end host wants to send a packet, it inquires the path server and obtains an authorized segment.
Its signatures are stripped off and the information extracted is a path description and hop authenticators (σs). A path description is a sequence of hop information (H I). The source constructs the packet from this acquired data and the payload. It calculates hop validation fields (HVF) using σs, which are used for authentication. In this protocol, each HVF is simply equal to the corresponding σ. For example, if we take the network from Figure 2.2 and we suppose that an end host H
Sat the AS W wants to send a packet to an end host H
Dat Z, the packet would include the following information.
packet = ( src || dest || path || validation || payload ) src = ( W || H
S)
dest = ( Z || H
D)
path = ( H I
W|| H I
X|| H I
Y|| H I
Z)
validation = ( HVF
W|| HVF
X|| HVF
Y|| HVF
Z) = ( σ
W|| σ
X|| σ
Y|| σ
Z)
The source sends this packet on its path. It also contains a pointer indicating the current hop.
Every AS on the path checks whether the packet was received by the egress interface stated in
2.1. SCION H I, recomputes its HVF, and checks whether it matches the HVF in the packet. The packet is forwarded by the ingress interface from H I only if all checks succeed. In the initial SCION dataplane design, the HVF is a MAC of H I of the current and previous ASes and the HVF of the previous AS.
H I = ( IgIF || ID || EgIF )
HVF
X= σ
X= MAC
KX( H I
X|| H I
Y|| HVF
Y) [[ 0 : l
v]]
X is the current AS, Y is the previous one in the direction of beaconing, i.e. top-to-bottom.
These are simplified versions of the computations, omitting some fields that contain public information, which does not affect the security properties or info needed for transfer outside the scope of this work.
The interfaces are ingress (i.e., entrance) and egress (i.e., exit) for the beacon, however, the data transfer happens in the opposite direction. Therefore the packets enter the AS through the egress interface and leave through the ingress interface. This has to be kept in mind to avoid getting confused.
2.1.3 Implementation by Anapaya
The controlplane and dataplane protocols in SCION were designed as described above in Section 2.1.1 and Section 2.1.2, however, the actual implementation by Anapaya [2] includes slightly altered protocols. They utilize exclusive-or (XOR) to accumulate σs. A new variable β is introduced, which is initialized as a random number, recorded in β
0.
In the controlplane, a newly created PCB includes β
0. At every AS, σ is computed as a MAC of H I and the current β. Then, the next β is computed as XOR of truncated σ and the previous value of β. For example, at the AS Y, it is computed as follows.
σ
Y= MAC
KY( H I
Y|| β
Y) β
X= β
Y⊕ σ
Y[[ 0 : 2 ]]
In the dataplane, HVF is again equal to σ. Every AS on the path updates the value of β and then recomputes HVF as follows.
β
Y= β
X⊕ HVF
Y[[ 0 : 2 ]]
HVF
Y0= MAC
KY( H I
Y|| β
Y)
An incoming packet includes the expected HVF
Yand the current β
X. First, β
Yis computed with the HVF
Yfrom the input. Then, with the newly computed β
Y, HVF
Y0is recomputed by the AS and compared to the expected HVF
Y. The packet is only accepted and forwarded if it was received on the interface contained in H I
Yand HVF
Y= HVF
Y0.
This new protocol seems to be more complicated since it introduces a new variable, but in
practice, it is supposed to run faster. This is mainly due to limiting the number of conditional
statements needed in the implementation. However, it can be more complicated to prove its
security properties, especially since XOR is used, which has several algebraic properties that
an attacker may try to exploit. These are further described in Section 2.4.1. Using XOR opens
up many uncertainties, for example, what if at some point the variable β could become zero
and the adversary could use that to its advantage. The initial design included only a MAC,
which is one-way, and therefore it is easy to argue about in a security proof.
2.2 EPIC
EPIC [3] is a family of dataplane protocols that can be used in SCION, but also other future Internet architectures. These protocols provide stronger security properties than the initial SCION dataplane protocol or other existing dataplane protocols. They are aiming to make the Internet path-aware. This improved security does not come at the expense of efficiency. The acronym stands for ”every packet is checked” and that is because these protocols achieve their security properties by checking every single packet. It has 4 different levels, with increasingly stronger security.
2.2.1 Level 0
The zeroth level is almost identical to the original SCION design. The only difference for our purposes is that it omits the H I
Yin the MAC when computing σ. The σ computation is done as follows.
σ
X= MAC
KX( H I
X|| σ
Y) [[ 0 : l
v]]
The only target security property is path authorization. Even though H I
Yis omitted, path authorization still holds, which will be verified in this work. Intuitively, it is because the MAC also contains σ
Y, which contains H I
Y, therefore including it twice is redundant.
2.2.2 Level 1
One shortcoming of the EPIC L0 protocol is that the σ is reused as an HVF for all packets traveling the same path. It is therefore vulnerable to brute-force attacks, especially if l
vis made small for the sake of efficiency. The first level of EPIC solves this by using per-packet HVFs that include a unique timestamp of the packet. Level 1 introduces the following vari- ables: a segment identifier S and a validation field V. They are used when calculating per-packet HVFs.
In the controlplane, σs are calculated as follows. For the the first core AS, let us say Z, it is calculated as a MAC of just H I
Z. For all of the other ASes, it is calculated as a MAC of H I and the previous S, which is just a truncated σ. So, for the first three ASes Z, Y and X, σs are calculated as follows.
σ
Z= MAC
KZ( H I
Z) S
Z= σ
Z[[ 0 : l
s]]
σ
Y= MAC
KY( H I
Y|| S
Z) S
Y= σ
Y[[ 0 : l
s]]
σ
X= MAC
KX( H I
X|| S
Y)
In the dataplane, a new variable V is added to the HVF, ensuring that HVF is unique for each packet. The source of a packet receives the path description and the σs from a path server. It calculates all HVFs as follows. First, it generates a packet timestamp ts
pkt. Then, it computes V as a MAC of the timestamp and the source. The key used for the MAC is σ.
Finally, S and V are concatenated to create the HVF.
2.2. EPIC
V
X= MAC
σX( ts
pkt|| src )[[ 0 : l
v]]
S
X= σ
X[[ 0 : l
s]]
HVF
X= S
X|| V
XAs the packet traverses a network, each AS on the path recomputes its HVF and checks whether it matches the HVF included in the packet. The target security property is path authorization. A potential attack on path authorization is if an attacker can craft HVF for a link that is not authorized without knowing the MAC key K
X. They can try guessing this HVF in a brute-force attack. Even if the attacker successfully guesses one HVF, it will only be valid for one timestamp. So, the attacker can only send packets with the same reused timestamp, however, this can be easily detected by a replay-suppression system. Being able to send a single packet by an unauthorized link is not assumed to be a real threat to the protocol.
Therefore, the benefit of the EPIC L1 protocol compared to the EPIC L0 protocol or the initial SCION protocol is that the value l
vcan be quite small, which helps its efficiency.
2.2.3 Level 2
The second level introduces new shared keys that provide the ability to authenticate the packet and the source. The shared key K
BAis a key shared between the ASes A and B. It is a Dynamically Recreatable Key (DRKey) [6], meaning it is derived from the secret key of the AS B by a pseudorandom function (PRF). This ensures that the AS B can recompute the key K
BAfaster than fetching it from a key store. The AS A has to securely fetch it from a key store in order to use it.
K
BA= PRF
KB( A )
The controlplane collects the same information as in the EPIC L1 protocol. The difference is how the source calculates HVF. Instead of using σ
Xas the key for the MAC in V
X, it uses the key K
SXand σ
Xin included in the contents of the MAC. So, the source computes HVF as follows.
σ
X= MAC
KX( H I
X|| S
Y) S
X= σ [[ 0 : l
s]]
V
X= MAC
KSX
( ts
pkt|| src || σ
X) [[ 0 : l
v]]
HVF
X= S
X|| V
XThis key K
SXis shared between the AS X and the source S. AS X is able to quickly derive the shared key K
SXand therefore authenticate the source S, since only those two entities have access to the key. The source has to securely fetch all of these shared keys from a key store in order to compute HVFs.
The derivation of these DRKeys is simplified for the purpose of this work. Here, the keys are
only dependent on the ASes, however, they should also be dependent on the end hosts. You
will see later that we are not distinguishing end hosts and their ASes, therefore we can allow
this simplification. Furthermore, in real life, the shared key would probably not be derived
directly from the MAC key. Each AS would have a secret master key, from which all other
keys would be derived, including the MAC key and the DRKey. However, we can model the protocol without this more complex key management system.
Another new component that the source computes and includes in the packet is a destination validation field V
SD. Its purpose is for the destination to be able to authenticate the packet. It is computed by the source as a MAC of the packet timestamp, the path, and the payload. The MAC key used is K
SD, a DRKey shared only between the source and the destination.
V
SD= MAC
KSD
( ts
pkt|| path || payload )
Every on-path AS X recomputes the key K
SXand subsequently recomputes HVF
Xand checks whether it matches the HVF
Xincluded in the packet. The destination makes an additional check by recomputing V
SDand checking whether it matches the V
SDincluded in the packet.
The target security properties of this protocol are path authorization, packet authentication, and source authentication.
2.2.4 Level 3
In the third level, on-path ASes not only check the validation fields, but they overwrite them to prove that they were indeed on the path and they processed the packet. The controlplane is again the same. Let us define C
Xas a MAC of the packet timestamp, the source, and the σ, using the key shared between the current AS and the source. This is equal to how the variable V
Xis defined in the EPIC L2 protocol but without truncation. Now, we define V
X0to be equal to the first l
vbytes of C
Xand V
X1to be equal to the next l
vbytes, assuming that the C
Xhas at least 2l
vbytes.
C
X= MAC
KSX
( ts
pkt|| src || σ
X) V
X0= C
X[[ 0 : l
v]]
V
X1= C
X[[ l
v: 2l
v]]
AS autonomous system ISD isolation domain
PCB path-segment construction beacon H I hop information
HVF hop validation field K
Xsecret key of X
MAC
Kmessage authentication code using key K IgIF ingress interface
EgIF egress interface σ hop authenticator S
Xsegment identifier V
Xvalidation field
K
YXshared DRKey between X and Y, which can be efficiently calculated by X PRF
Kpseudorandom function using key K
V
SDdestination validation field
Table 2.1: Abbreviations and notations
2.3. Security Properties In the dataplane, the sender includes V
0s in the packet’s HVFs. Each AS X on the path first recomputes its C
Xand compares the computed V
X0to the one included in the packet in the HVF
X. Then, it replaces V
X0with V
X10as a proof that the packet traverses the AS X.
These new validation fields V
1s are also added to the destination validation field V
SD. The source includes the V
1s for all ASes on the path that is intended for the packet.
V
SD= MAC
KSD