Research Collection
Doctoral Thesis
Advancing the Formal Foundations for Voting Protocols
Author(s):
Schmid, Lara Publication Date:
2020-06
Permanent Link:
https://doi.org/10.3929/ethz-b-000418853
Rights / License:
In Copyright - Non-Commercial Use Permitted
This page was generated automatically upon download from the ETH Zurich Research Collection. For more information please consult the Terms of use.
ETH Library
Diss. ETH No. 26770
Advancing the Formal Foundations for Voting Protocols
A thesis submitted to attain the degree of DOCTOR OF SCIENCES of ETH Z
URICH(Dr. sc. ETH Zurich)
presented by
L
ARAA
LEXANDRAS
CHMIDMSc ETH in Computer Science, ETH Zurich born on 24.04.1990
citizen of Gipf-Oberfrick AG
accepted on the recommendation of Prof. Dr. David Basin, examiner Prof. Dr. Kenny Paterson, co-examiner
Dr. Saša Radomirovi´c, co-examiner Prof. Dr. Peter Y. A. Ryan, co-examiner
2020
Abstract
Elections are the foundation of democracy. Following the global wave of digitalization, countless electronic voting, also called e-voting, procedures have been proposed where at least parts of the elections are realized elec- tronically. Compared to purely paper-based voting, e-voting is supposed to enhance usability and accessibility, thereby increase the voter turnout, and ultimately strengthen democracy. Furthermore, e-voting enables new alternative forms of democracy, for examplerandom sample voting, where only a randomly chosen subset of all eligible voters, thesample group, are selected to vote. Random sample voting allows to choose the sample group size such that an election’s result accurately reflects the opinion of the entire electorate while the election’s cost is lower than in elections where each voter votes. Moreover, in random sample voting voters vote less frequently and can thus spend more time and resources to inform themselves prior to casting a vote. Therefore, random sample voting promises to further increase the utility of e-voting.
Despite these benefits, so far e-voting procedures have primarily made headlines as insecure or untrustworthy. Designing secure e-voting pro- cedures is non-trivial as they must satisfy a challenging combination of security properties in the presence of strong adversaries. Moreover, in con- trast to other security protocols, voting procedures involve human voters as endpoints, which are fallible and computationally weaker than machines.
In this thesis, we aim to advance voting by proposing the design of a ran- dom sample voting protocol and by providing new formal foundations for reasoning about voting protocols, their security properties, and their system assumptions. In detail, we make the following contributions.
First, we propose Alethea, the first random sample voting protocol that satisfies end-to-end verifiability and receipt-freeness. We define new security properties related to the unpredictability and anonymity of the sample group as well as properties bounding the probability of undetected manipulations. Then, we formally prove thatAletheasatisfies these new properties as well as conventional properties for e-voting.
Our second contribution considers disputes, which arise when a voter claims that his ballot was not correctly included in the tally while the authority running the election claims to have followed the protocol. The propertydispute resolutionstates that a voter who detects manipulations must be able to convince everyone else that the authority is dishonest, whereas an honest authority cannot be wrongly convicted. We consider this
ii
property not only for random sample or electronic voting, but for a generic class of voting protocols. We propose a new, formal definition of dispute resolution that includes a notion of timeliness and considers disputes not covered by previous definitions. We then fully characterize what system and adversary assumptions are necessary and sufficient for the timeliness property to hold.
Finally, we provide a model for formalizing and reasoning about the inherent human limitations and their consequences for the security of protocols. This model is not specific to but particularly relevant for voting protocols, where human voters are the endpoints. Our model distinguishes the human users from their devices and also allows for human errors. This enables more fine-grained statements about the required capabilities of each agent than is possible in previous work. In particular, our model allows us to compare different protocols with respect to their robustness against human errors. This enables the classification of security protocols from a usable-security perspective.
We model all introduced protocols, their security properties, as well as the system and adversary assumptions in a symbolic formalism that can be used as input language to the Tamarin tool. We then prove the correctness of the protocols by combining automatic machine-checked proofs with traditional pen-and-paper proofs. This combination of automated and manual proofs allows us to prove all relevant security properties while benefiting from automation in many cases.
Zusammenfassung
Wahlen sind die Grundlage der Demokratie. Im Zuge der globalen Digitali- sierung wurden unzählige Wahlverfahren vorgeschlagen, welche zumindest zum Teil elektronisch umgesetzt werden. Solche Verfahren werden auch E-Voting-Verfahren genannt. Im Vergleich zu rein papierbasierten Verfahren, versprechen E-Voting-Verfahren durch eine bessere Benutzerfreundlichkeit und Zugänglichkeit die Wahlbeteiligungen zu steigern und somit Demokra- tien zu stärken. Ausserdem ermöglicht E-Voting neue alternative Formen der Demokratie. Zu diesen zählen zum BeispielRandom Sample Voting Verfahren, in denen nur eine zufällige Untermenge aller Wahlberechtig- ten ausgewählt wird, welche dann abstimmen dürfen. In Random Sample Voting können so viele Wähler zufällig bestimmt werden, so dass das Wahl- ergebnis zuverlässig die Meinung der ganzen Wählerschaft widerspiegelt, während die Kosten der Wahl niedriger sind als bei Wahlen, bei denen alle Wähler eine Stimme abgeben. Des Weiteren müssen die Wähler in Random Sample Voting weniger häufig abstimmen und können dadurch mehr Zeit und Ressourcen aufwenden, um sich vor der Stimmabgabe zu informieren.
Deshalb könnte Random Sample Voting den Nutzen von E-Voting noch weiter steigern.
Trotz all dieser Vorteile, haben E-Voting-Verfahren bisher vor allem negative Schlagzeilen ausgelöst. Darin wurde aufgedeckt, dass sie unsi- cher und nicht vertrauenswürdig waren. Die Entwicklung von sicheren E-Voting-Verfahren ist nicht trivial, weil solche Verfahren anspruchsvolle Kombinationen von Sicherheitseigenschaften im Angesicht von starken Angreifern erfüllen müssen. Dazu kommt, dass im Gegensatz zu anderen Sicherheitsprotokollen bei Wahlverfahren menschliche Wähler involviert sind, welche Fehler begehen und rechnerisch schwächer sind als Maschinen.
Diese Arbeit hat das Ziel Wahlverfahren weiterzuentwickeln, indem wir ein neues Random Sample Voting Verfahren präsentieren, sowie neue formale Grundlagen schaffen, um Wahlverfahren, ihre Sicherheitseigenschaften und ihre Annahmen zu ergründen. Insbesondere präsentieren wir die folgenden Beiträge:
Wir präsentierenAlethea, das erste Random Sample Voting Verfahren welches Ende-zu-Ende verifizierbar und “receipt-free” ist. Wir definieren neue Sicherheitseigenschaften, welche die Unvorhersehbarkeit und An- onymität der zufällig gewählten Wählergruppe beschreiben, sowie Eigen- schaften welche die Wahrscheinlichkeit von unerkannten Manipulationen
iv
beschränken. Danach beweisen wir formal, dassAletheadiese, sowie kon- ventionelle Eigenschaften für E-Voting erfüllt.
Unser zweiter Beitrag betrifft Konflikte, welche auftreten, wenn ein Wähler behauptet, dass sein Wahlzettel nicht richtig im Wahlresultat be- rücksichtigt wurde, während die Behörde, welche die Wahl durchführt, angibt, sich nach dem Protokoll verhalten zu haben. Die EigenschaftDispute Resolutionfordert, dass ein Wähler, welcher Manipulationen entdeckt, in der Lage ist, alle zu überzeugen, dass die Behörde unehrlich ist. Gleichzeitig soll es nicht möglich sein, dass eine ehrliche Behörde fälschlicherweise verurteilt wird. Wir untersuchen diese Eigenschaft nicht nur für Random Sample Voting oder für E-Voting, sondern für eine allgemeine Klasse von Wahlprotokollen. Wir präsentieren eine neue formale Definition von Dispute Resolution, welche eine Art von Rechtzeitigkeit fordert und berücksichti- gen dabei Konflikte, welche von vorherigen Definitionen nicht abgedeckt wurden. Wir charakterisieren dann vollständig welche Annahmen bezüg- lich des Systems und Angreifers nötig und ausreichend sind, damit die Rechtzeitigkeitseigenschaft erreicht werden kann.
Schliesslich präsentieren wir ein Modell zur Formalisierung der limitier- ten menschlichen Fähigkeiten und deren Konsequenzen für die Sicherheit von Protokollen. Dieses Modell ist nicht nur für Wahlprotokolle geeignet, aber für diese besonders wichtig, weil in Wahlprotokollen menschliche Wäh- ler die Endpunkte bilden. Unser Modell unterscheidet die menschlichen Nutzer von deren Geräten und erlaubt zudem menschliche Fehler. Dies ermöglicht es uns, genauere Aussagen über die nötigen Fähigkeiten der ein- zelnen Agenten zu machen, als dies in vorherigen Arbeiten möglich war. Ins- besondere ermöglicht unser Modell den Vergleich verschiedener Protokolle im Bezug auf deren Robustheit gegenüber verschiedenen menschlichen Fehlern. Dies ermöglicht eine Klassifizierung von Sicherheitsprotokollen unter dem Usable-Security-Aspekt, das heisst, wie benutzerfreundlich und sicher sie sind.
Wir modellieren alle eingeführten Protokolle, deren Sicherheitseigen- schaften und die zu Grunde liegenden System- und Angreifer-Annahmen in einem symbolischen Formalismus, welcher auch als Eingabesprache für das Tamarin Tool dient. Wir beweisen dann die Korrektheit aller Protokolle, indem wir automatische Beweise mit traditionellen Beweisen von Hand verknüpfen. Diese Kombination von automatischen und manuellen Bewei- sen erlaubt es uns alle relevanten Sicherheitseigenschaften zu beweisen, während wir in vielen Fällen von der Automatisierung profitieren.
Acknowledgments
First, I would like to thank David Basin for believing in my potential and giving me the opportunity to write this thesis in his group. Despite his full schedule he always found time to provide feedback to all my ideas and reports, to discuss projects, and to share valuable advice both on research and also on life in general. David’s guidance was invaluable and his enthusiasm for research was inspiring. I also wish to express my appreciation and gratitude to Saša Radomirovi´c, who was the supervisor of my Master’s thesis and has stayed an appreciated mentor ever since. I thank him for the countless hours of meetings, for reading all my proofs, but mostly for insightful discussions on all issues no matter how big or small. I am also very grateful to Kenny Paterson and Peter Y. A. Ryan for agreeing to be in my committee, for investing the time and effort to read my thesis, and for providing me with interesting feedback.
I had the pleasure working with many brilliant, kind, and fun people.
I would like to thank all current and past members of the Institute of Information Security for contributing to an absolutely enjoyable working environment. A lot of them became dear friends over the years. I wish to express special thanks to Ralf Sasse for always taking time for my Tamarin questions and to Vivien Klomp, Barbara Pfändner, and Saskia Wolf for providing prompt and friendly help on all administrative matters (and for making sure I have enough coffee). Moreover, I would like to thank my long term office mates Ognjen Mari´c who thought me how to be a PhD student and that a fancy office chair is key to success, Lucca Hirschi with whom I had many interesting discussions that lead to a collaboration that I still enjoy, and Sven Hammann who always compassionately shared my sentiments both about rejected papers and small successes. I also thank the students that did a project with me and contributed to the further development of my research ideas.
Finally, I am deeply grateful for my family and friends, mostly those who became both over the years, and would like to thank them for their endless love and support. Especially, I would like to thank my dad (I’ll try to always live by your advice and your example), my mum and brother, the unconditional cheerleaders of my life (“you’ll be in my heart”), and my partner in crime, the main technical and emotional support during the writing of this thesis and in my life (you’re the best).
Contents
1 Introduction 1
1.1 Open Problems . . . 2
1.2 Contributions . . . 6
1.3 Publications . . . 10
1.4 Organization and Structure . . . 11
2 Protocol Model 13 2.1 Term Algebra and Notation . . . 13
2.2 Protocol Specification . . . 15
2.3 System Setup and Adversary Model . . . 19
2.4 Execution Model . . . 23
2.5 Security Properties and Restrictions . . . 24
2.6 Tamarin Protocol Model . . . 26
3 Alethea: A Provably Secure Random Sample Voting Protocol 35 3.1 Setup and Adversary Assumptions . . . 36
3.2 Protocol . . . 39
3.3 Analysis . . . 49
3.4 Alethea-D: An Alternative toAlethea’s Selection Phase . . . . 67
3.5 Related Work . . . 75
3.6 Mass Elections and Outlook . . . 79
4 Dispute Resolution in Voting Protocols 81 4.1 Protocol Model Extensions . . . 82
4.2 Class of Voting Protocols . . . 86
4.3 Dispute Resolution . . . 90
4.4 Communication Topologies and Timeliness . . . 97
4.5 Dispute Resolution in Practice . . . 101
4.6 Related Work . . . 110
5 Human Errors in Security Protocols 115 5.1 Approaches to Defining Fallible Humans . . . 116
5.2 Formally Modeling Fallible Humans . . . 118
5.3 Case Studies on Authentication Protocols . . . 128
5.4 Explicit Signals in the Human Role . . . 145
5.5 Verifiability inAlethea-D’s Voting Phase with Human Errors 159 5.6 Related Work . . . 165
viii Contents
6 Conclusion and Future Work 169
6.1 Summary of Contributions . . . 169 6.2 Future Directions . . . 171
A AletheaandAlethea-D 175
A.1 Proofs forAlethea . . . 175 A.2 Proofs forAlethea-D. . . 185
B Dispute Resolution 191
B.1 Proofs from Section 4.4 . . . 191 B.2 Proofs from Section 4.5 . . . 214
C Human Errors 227
C.1 Remaining Untrained-Human Rules . . . 227 C.2 MP-Auth_MAwith Rule-Based Humans . . . 228 C.3 Authentication Protocols from the Case Study . . . 232
List of Figures
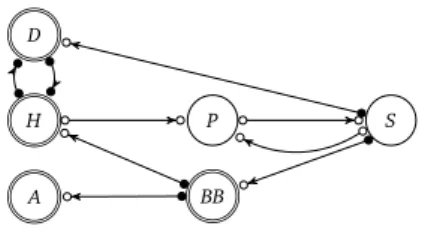
2.1 The protocolSimpleVote, or PrSV for short, wherepkS = pk(skS). . . 17 2.2 Whereas the topology graph depicts the system setup, the
topology additionally depicts the adversary assumptions in terms of trust and channel assumptions. . . 20 2.3 The trace setsTR(PrSV,TSV)andPropSV when the protocol
PrSV run in the topologyTSV (a) satisfies and (b) does not satisfy the propertyPropSV. The red traces in (b) are attack traces that violate the propertyPropSV. . . 25 2.4 The setup rule and the agent rules for the protocolSimpleVote
from Figure 2.1. . . 31 3.1 The communication topologyTALthat we assume forAlethea,
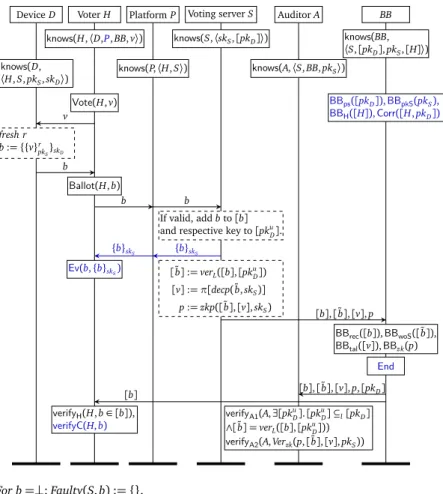
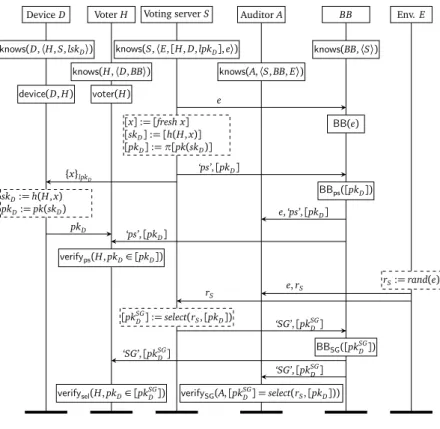
except for privacy properties, where we additionally assume thatSis trusted. . . 36 3.2 Alethea’s selection phase, wherelpkD=pk(lskD)denotes the
deviceD’s long term public key. . . . 43 3.3 Alethea’s voting phase, whereskD=h(H,x)is a voter’s sign-
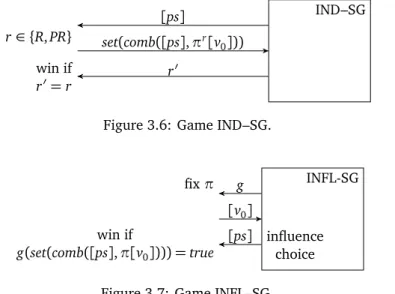
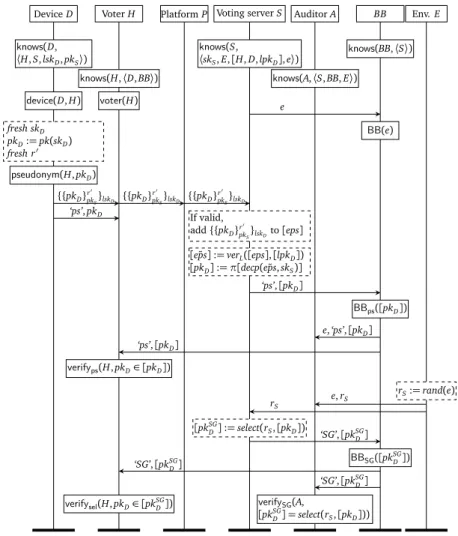
ing key andpkD=pk(skD)the corresponding verification key that serves as the voter’s pseudonym. The lists[skSGD ] and[pkSGD ]respectively contain such a signing and verifica- tion keys for each sample voter.pkS=pk(skS)denotesS’s public key. . . 46 3.4 Game RP-PRP. . . 62 3.5 Game IND–SG–out, where[ps]is a list of pseudonyms. . . 64 3.6 Game IND–SG. . . 65 3.7 Game INFL–SG. . . 65 3.8 Alethea-D’s selection phase, wherelpkD=pk(lskD)denotes
device D’s long term verification key and pkS = pk(skS) denotesS’s public encryption key. . . . 68 4.1 We allow for any topology whereG(T)⊆GGS orG(T)⊆GGU. 87 4.2 Possible disputes in voting. The authority’s claim is captured
by the information on the bulletin board. The respective disputes can be resolved when all properties in the third and fourth column hold. . . 92
x List of Figures 4.3 The minimal topologies for which there exists a protocol
such thatTimelyDRcan be achieved. . . 99
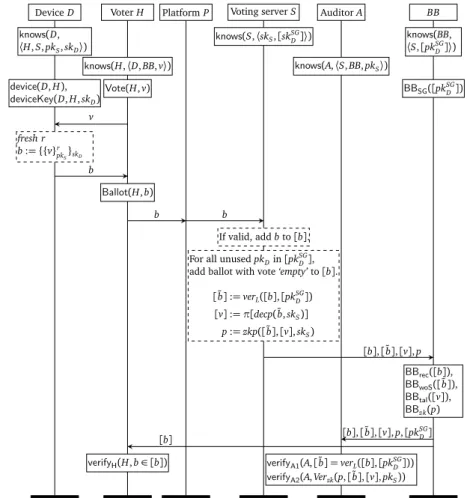
4.4 The topologyTDRfor the protocolAlethea-DR. . . 104
4.5 The protocolAlethea-DR, which is similar toAlethea-D’s vot- ing phase but contains additional messages and signals shown in blue. It holds that pkD = pk(skD) and pkS = pk(skS). . . 105
5.1 Skilled and rule-based human approaches: Black and gray nodes represent skilled and rule-based humans, respectively. An arrow denotes that the human at the tail node induces only a subset of the system behaviors that the human at the arrow’s tip induces. . . 117
5.2 An example protocol used to demonstrate the tags. . . 121
5.3 Untrained-human rules for producing fresh messages, send- ing messages to and receiving messages from an insecure channel. . . 122
5.4 Trace restrictions modeling guidelines of a rule-based human.125 5.5 The default communication topology for the authentication protocols considered in this section. . . 128
5.6 The topologyTMPfor the protocolMP-Auth. . . 132
5.7 TheMP-Authprotocol, wherepkS=pk(skS). . . 132
5.8 TheMP-Auth_MAprotocol, wherepkS=pk(skS). . . 135
5.9 The human voter role ofAlethea-D’s voting phase. . . 148
5.10 Mechanical transformation of a protocolPrand a property Propsuch that they can afterward be analyzed with any kind of human. . . 155
5.11 Transformation of the human role to account for human errors in the example protocolHPagree, where a non-human rolePwants to establish agreement with a human roleH. . 156
5.12 Trace restrictions modeling guidelines used in the analysis ofAlethea-D’s voting phase. . . 162
A.1 Reduction from the game RP–PRP to the game IND–SG–out. 183 A.2 Reduction from the game RP–PRP to the game IND–SG. . . 184
A.3 Reduction from the game RP–PRP to the game INFL–SG. . . 185
B.1 Topologies for which it is impossible to achieveTimelyDRby Lemma 37. . . 202
B.2 Topologies for which it is impossible to achieveTimelyDRby Lemma 39. . . 206
List of Figures xi
B.3 The protocolPr1. . . 208
B.4 The protocolPr2. . . 209
B.5 The protocolPr3. . . 210
B.6 The protocolPr4. . . 211
B.7 The protocolPr5. . . 212
B.8 The protocolPr6. . . 213
B.9 The protocolPr7. . . 214
C.1 Untrained-human rules for sending messages to and receiv- ing messages from authentic, confidential, and secure chan- nels. . . 227
C.2 A trace ofMP-Auth_MAviolating message authentication. The implicit signalsKrecording the adversary’s knowledge are not shown for readability. Multisets of signals are de- noted by{}b. . . 230
C.3 The topology for the protocolCronto. . . 233
C.4 The protocolCronto. . . 233
C.5 The protocolCronto_MA. . . 234
C.6 The topology for the protocolsGoogle 2-StepandOTP over SMS. . . 235
C.7 The protocolGoogle 2-Step. . . 235
C.8 The protocolOTP over SMS . . . 236
C.9 The topology for the protocolPhoolproof. . . 237
C.10 The protocolPhoolproof, wherepkS =pk(skS)andpkD= pk(skD). . . 237
C.11 The topology for the protocolSound-Proof. . . 238
C.12 The protocolSound-Proof, wherepkD=pk(skD). . . 239
List of Tables
5.1 Entity authentication (EntityAuth), device authentication (DeviceAuth), and message authentication (MsgAuth) of hu- manHto serverS, with an infallible (I), untrained (U), and rule-based (R-B) human. . . 141 5.2 Summary of the analysis ofAlethea-Dwith one voter who
is infallible (I), untrained (U), or rule-based (R-B) and with a voting server who is trusted (trustedS) or untrusted (un- trustedS). . . 161 B.1 Overview table of the results from Theorem 3 showing how
each of the properties (in the first column) is proven in each of the topologiesTDRS+H+,TDRH+, andTDRS+ for a fixed number of voters (denoted byfixed) and for an arbitrary number of voters (denoted byany).TandT(2)denote that the property is proven with Tamarin for one or two voters respectively, H(LX) that the property is proven by hand (in an extra LemmaX), – that the property is not shown for this number of voters as this is not needed or implied by the other results, and×that the property is not proven as it is not required for the theorem to hold. . . 216
Chapter 1
Introduction
Voting is a method for a group of people to collectively make decisions.
Even though voting is used in various contexts, it is particularly impor- tant and delicate as it is also used in democratic elections, for example to appoint members of the parliament or decide whether new laws should be implemented. That is, voting constitutes an important foundation of democracies. Following the trend of digitalization, different voting proce- dures have been proposed where at least parts of the procedure are run by machines. Such voting procedures are calledelectronic votingore-voting procedures.
In the past, several countries, including Brazil, India, and the United States[51], have deployed e-voting inpoll-sitevoting procedures. In such procedures, voters go to a polling station where they cast their ballot with the help of a machine. For example, they scan their paper ballot on an optical scanner or enter their ballot on a direct-recording electronic (DRE) voting machine. More recently, also differentremotee-voting procedures have been deployed, where ballots are cast remotely. They have been used, for example, in academia and organizations to elect holders for different positions[5, 13]. Moreover, remote procedures have been used, or at least been tested, for several binding democratic elections, for example in Estonia[62], New South Wales [22, 33], and Switzerland[60, 83].
One of the main advantages of e-voting compared to fully paper-based voting is that the results can be computed faster and more accurately by machines. Moreover, e-voting can improve the accessibility of voting procedures, for example by enabling disabled voters to vote independently or by allowing voters who are distant from polling stations to vote remotely.
Furthermore, when ballots are entered on machines, the machines can check them and warn voters when their ballots do not adhere to a required format or when they are unreadable. Despite these advantages, the introduction of e-voting for democratic elections is highly controversial. The main reason for this is that it has repeatedly been shown that existing, deployed e-voting procedures have severe flaws that allow attackers to change the election result or learn how voters voted[40, 98, 101, 102, 61].
There are different reasons why the design of secure e-voting procedures is hard. First, as elections are used to decide on highly critical matters with possibly severe implications, voters must be able to freely choose their vote without feeling threatened to later being blamed for it. Thus,
2 1 Introduction e-voting procedures must preserveprivacy, that is they must not reveal how each voter voted. Second, for a society to accept a voting procedure, the public must believe that the system implementing it works as intended, that is, the system must betrustworthy. This is essential as elections involve participants from opposing political parties that may neither trust each other nor the (current) government running the election. Thus, voters and auditors must be able toverifythat the procedure behaves as specified and detect any manipulations, even if they do not trust the authority running the election. A third challenge is that powerful entities, such as external nation states or insiders providing the election infrastructure, may profit from certain election outcomes. That is, extremely well-equipped and motivated adversaries might attempt to influence elections or threaten voters. Therefore, voting procedures must be secure even in the presence of such strong adversaries.
As voting procedures are complex and critical, it is necessary to precisely reason about whether and how they can be designed to achieve the required security properties under different adversary models. Such reasoning requires formally defining theprotocolsthat specify the involved parties’
behaviors, the exactsecurity propertiesthat are aspired, and thesetup and adversary assumptionsunder which these properties should be met. We next present open problems with respect to each of those three components and afterward present how this thesis contributes to their solution.
1.1 Open Problems
1.1.1 New Voting Protocols
Plenty of e-voting protocols have been proposed. A lot of poll-site proto- cols[86, 28, 82, 87, 41, 31]focus on providing voters with a receipt that they can take home and later compare with the information on a public bulletin board, thereby verifying that their vote was included in the tallying process. These receipts must be designed carefully to ensure that they do not break vote privacy. Most remote e-voting protocols that aim at achieving both privacy and verifiability, either use homomorphic encryp- tion[38, 36, 27]or mix-nets[4, 32, 65, 88]to compute the tally from a set of encrypted votes in a verifiable but privacy preserving manner. Even though the mentioned voting protocols have different goals and consider different settings, they are all designed formass elections, where all voters of the electorate are allowed to vote.
Recently, and partially motivated by the new possibilities of e-voting, researchers in political economy have studied what qualities constitute
1.1 Open Problems 3 good elections. Whereas the purpose of a democratic election is to reach a decision based on the will of the voters, mass elections may not be the best way to achieve this goal. For example, direct democracy is expensive and the voters do not have the resources to make well informed decisions on all matters they can vote for. Consequently, alternative forms of democracy have been proposed[30, 54, 70, 71]. One of these proposed new forms of democracy israndom sample voting, where only a randomly chosen subset of the electorate, thesample group, votes. Intuitively, while the smaller number of voters makes random sample voting cheaper and thus more efficient than mass elections, the election outcome should accurately reflect the will of the entire electorate when the sample group is chosen randomly.
For the advantages of random sample voting to be effective, it should be realized by a remote (e-)voting protocol, as otherwise adversaries could attempt to influence the few voters prior to casting their vote at a polling station.
Whereas the study of new forms of democracy and their benefits is an active research area in political economy, it also raises interesting new questions from a protocol security perspective.
Open problems: How can a secure and practical remote voting protocol be designed for random sample voting?
1.1.2 New Security Properties
Traditionally, voting protocols mainly aim at satisfying two kinds of prop- erties. First, privacy properties state that the adversary must not learn how voters voted and different notions thereof have been formalized in prior work (e.g.,[15, 42, 43, 47, 65]). Thereby, the following different levels of privacy are often distinguished. (Vote) privacydenotes that the adversary cannot link a voter to his vote[42, 43].Receipt-freenessdenotes that a voter cannot prove to an adversary how he voted, even when he is willing to reveal all his secrets[42, 43]. This property is strictly stronger than vote privacy as it also protects honest voters who may be forced to reveal private information. Finally, an even stronger property iscoercion resistance, which denotes that the adversary cannot learn how or whether a voter voted, even when the adversary can provide the voter with input and learn secrets from the voter during the election[42, 43, 65].
The second kind of property that voting protocols aim at is verifiabil- ity, which denotes that any manipulation of the election is detectable by some honest party. To achieve this, the information relevant for checking
4 1 Introduction verifiability may be published in a publicly accessible database, known as thebulletin board. Often this information contains the recorded (i.e., the collected) ballots and the election result. The gold-standard isend-to-end verifiability, which denotes that it is verifiable that the voter’s votes are correctly included in the final tally[69]. Usually, verifiability is divided into individualanduniversal verifiabilityproperties. The former denotes that each voter can verify, by performing some checks on the bulletin board, that his ballot is correctly recorded and thus considered in the tallying process[69]. We use the termuniversal verifiabilityfor properties that can be checked by anyone, for example, that the tally was computed correctly from all recorded ballots.1 Different notions of verifiability have been formalized, for example in[69]and[34];[37]provides an overview and comparison of several verifiability definitions.
Dispute resolution. Whereas verifiability ensures that any manipulation can be detected by some honest protocol participant, it does not ensure that all participants detect each manipulation. This is a problem in practice as only when the honest participants agree that manipulation happened can they take recovery measures. In particular, ballots are cast privately in elections. Thus only the voters themselves know if and how they voted and can perform the required checks for individual verifiability. Consequently, if a voter claims that his ballot is incorrectly recorded or that he was hindered in recording his ballot, no other party can know, a priori, whether the voter is lying or if there was a problem for which the authority running the election is responsible. We call such unresolved situationsdisputes. A protocol satisfiesdispute resolutionif any third party can unambiguously determine who is right in all disputes. For dispute resolution it is required that whenever a voter detects an anomaly, he is able to convince others that the authority is dishonest.2However, it must also be avoided that dishonest voters can convince others to convict an authority that behaved honestly.
The majority of formal analyses of e-voting protocols do not consider dispute resolution at all, e.g.,[4, 27, 32, 36]. Works that recognize the importance of dispute resolution[16, 7]or that take aspects of it into ac- count when proposing poll-site[17, 24, 25, 29, 41, 66, 96]or remote[103]
1Universal verifiabilityis sometimes used to only refer to the property that everyone can check that the final tally was correctly computed from all recorded ballots[69]. In contrast, we will call this propertytallied-as-recordedand use the termuniversal verifiabilityto collectively refer to all verifiability properties that can be checked by anyone.
2Here dishonesty includes all deviations of the authority from the protocol specification, both due to corruption or to errors.
1.1 Open Problems 5 voting protocols, reason about it only informally. The formal properties most closely related to dispute resolution are different notions ofaccount- ability[23, 72, 73]that formalize which agents should be held account- able when a protocol fails to satisfy some guarantees. These definitions are very general, but have been instantiated for selected voting proto- cols[23, 73, 74, 75]. However, the accountability properties satisfied by these protocols do not guarantee that a voter is able to convince others that the authority is dishonest in all situations where his ballot is not correctly recorded. In particular, in[23, 73, 75]there are unresolved disputes when a voter claims that he is not provided with a necessary confirmation from the authority to prove to others that he cast a ballot and the guarantees in[74]are even weaker. Thus, whereas properties must be defined pre- cisely to reason about whether they are achievable and by which means, there is currently no formal definition for dispute resolution that covers all relevant disputes in practice.
Open problem: What formal dispute resolution properties must hold in voting and under what system and adversary assumptions are they achievable?
Properties for new forms of democracy. Compared to traditional elec- tions, protocols for new forms of democracies must satisfy additional, new security properties. In particular, in random sample voting the selection of the sample group must be anonymous to avoid that sample voters are unduly influenced, harassed, or afterwards held responsible for an election outcome. Moreover, it must be ensured that no one (including the voting authority) is able to predict or influence the selection of the sample group and thereby bias the election result. Finally, the small number of selected voters leaves little room for error as only a few manipulations of votes may change the outcome. These observations raise the following question.
Open problem: What (new) security properties must be achieved by protocols realizing new forms of democracies such as random sample voting?
1.1.3 System Setups and the Human Voters
All voting protocols used in democracies involve humans, not machines, as endpoints. This means in particular that the required properties, such as end-to-end verifiability must hold from thehuman voters(as opposed to
6 1 Introduction their devices) to the, possibly remote, voting authority. The differences are critical: humans are not only computationally weaker than machines, they are naive, careless, and gullible. Taking these aspects into account when analyzing protocols has several consequences.
First, it is necessary to explicitly separate the roles of the human voter and his computing devices. Moreover, in remote Internet voting protocols, it should be assumed that general purpose platforms that are connected to the Internet are compromised. However, many existing remote Internet voting protocols that aim for strong properties do not separate the voter and its platform [27, 65] or require that the voter’s platform must be trusted[32]. Additionally, once we separate the voters and their devices, we must account for the fact that, unlike machines, humans cannot perform complicated computations, for example they cannot compute cryptographic functions[10].
Second, in contrast to protocols where only machines communicate with each other and precisely follow the protocol specification, human voters do not always understand what they should and should not do. Even knowledgeable voters may neglect to perform some protocol steps due to carelessness. Attackers, of course, are well aware of human fallibility and target humans in their attacks as it is often easiest to get information or access to a system by social engineering. For example, many people are fooled by phishing attacks into simply giving away their secret credentials.
Moreover, humans are bad at identifying phishing websites even when they are specifically instructed to do so in controlled lab environments[6, 45]. Therefore, it is unrealistic to assume that voters closely follow a given specification when analyzing voting protocols. Despite the severity of this problem, human weaknesses have received little attention in security protocol analysis, which raises the following question.
Open problem:How can the voters’ limited computational capabil- ities and human errors be taken into account in the formal analysis of voting protocols?
1.2 Contributions
In this thesis, we advance the state of the art by proposing a random sample voting protocol and by providing new formal foundations for the analysis of voting protocols. In particular, we make the following three contributions.
Design of a provably secure random sample voting protocol. We pro- poseAlethea, the first formally verified random sample voting protocol
1.2 Contributions 7 that satisfies end-to-end verifiability and receipt-freeness. To achieve differ- ent privacy properties, voters are identified by (anonymous) pseudonyms, which are in fact verification keys with associated signing keys. In a se- lection phase, a random subset of the eligible voters is selected based on their pseudonyms. Afterward, in a voting phase these selected voters can cast their votes, which are signed and can be authenticated by the voters’
pseudonyms. Our protocol makes explicit the distinction between human voters and their devices. This allows for fine-grained statements about the required capabilities and trust assumptions of each agent. Furthermore, instead of trusting general purpose platforms, we leverage special devices.
As they have limited capabilities and connectivity, it is more realistic to assume that such devices are trustworthy.
We formalize the properties that are necessary for and specific to random sample voting as well as conventional properties for e-voting. In particular, we define new security properties stating that the selection of the sample group cannot be predicted or influenced by anyone and must preserve the anonymity of the selected voters. Furthermore, as usually not all voters perform their individual verifiability checks in practice, we introduce the concept ofglobal verifiability propertiesthat express the probability that a cheating authority is not detected as a function of how many individual checks are made. We model the protocol and its properties symbolically and prove many of the properties using the Tamarin tool[79, 94]. We then complete the analysis with hand-written proofs for those properties that cannot be efficiently verified by any state-of-the-art tool and for properties that we prove on a lower level of abstraction than the symbolic model allows for. This combination of automated and manual proofs allows us to prove all relevant security properties while benefiting from automation in many cases.
In Alethea, the voting authority produces and therefore knows the voters’ pseudonyms. We will argue that this design has several advantages.
However, it also has disadvantages, for example that the authority can add or change ballots for those voters who do not perform their individual verifiability check. For this reason, we also propose an alternative variant of the protocol, calledAlethea-D, where the pseudonyms are produced by the voters’ devices rather than by the voting authority. We formally analyze all privacy and verifiability properties inAlethea-Dand present the trade-offs between the two variants of the protocol. In particular, we argue thatAletheais more usable whileAlethea-Dprovides additional security guarantees.
8 1 Introduction Dispute resolution in voting. As a second contribution, we provide a new foundation for characterizing, reasoning about, and establishing dis- pute resolution in voting. In contrast to the first contribution, this does not only consider random sample or electronic voting, but voting protocols in general. In particular, we systematically characterize all relevant disputes for a generic, practically relevant, class of voting protocols. Then, we focus on disputes regarding whether the published recorded ballots correctly represent the ballots cast by the voters. Based on our characterization, we propose a new formal definition of dispute resolution for voting that accounts for the possibility that both voters and the voting authority can make false claims and that voters may abstain from voting. We define that when a voter checks whether his cast ballot is correctly recorded, then either this is the case (respectively, no ballot is recorded when he abstained from voting) or he can convince others that the authority is dishonest.
At the same time, when the authority is honest, no dishonest voters can convince others of the contrary. This enables the analysis of a broad class of protocols with respect to dispute resolution.
A central aspect of our work is timeliness: when a voter’s ballot is recorded incorrectly, he should possess convincing evidence of this no later than by the election’s end. Especially, this includes scenarios where the authority hinders a voter from recording his ballot and thus ensures the resolution of disputes that could not be resolved unambiguously in prior work. We analyze what communication channels and trust assumptions are necessary and sufficient for timeliness. This results in a complete characterization of all communication topologies in our voting protocol class for which timeliness holds for some protocol. In particular, we show that timeliness can only be guaranteed under strong assumptions, for example some messages must not be lost on the network. Such a characterization can guide the design of new voting protocols where timeliness should hold, e.g., by identifying and thereby eliminating settings where timeliness is impossible.
To improve the feasibility of dispute resolution in practice, we introduce a property, calledUniqueness, that can be checked by everyone and guaran- tees that each recorded ballot was cast by a unique voter. We prove that in protocols where voters can cast at most one ballot,Uniquenessimplies dispute resolution guarantees for voters who abstain from voting. This has the practical consequence that in many protocols, the corresponding guarantees can be proven more easily. To demonstrate the applicability of our definitions, we analyze a variant ofAlethea-D’s voting phase with a dispute resolution procedure and prove that it satisfies all our defined
1.2 Contributions 9 dispute resolution properties while also preservingAlethea-D’s original security properties, including end-to-end verifiability and receipt-freeness.
We formalize the dispute resolution properties, the communication topologies, and the protocol in the case study symbolically using an exten- sion of the formalism from the first contribution, which is also supported by the Tamarin tool. To prove our claims, we then combine machine-checked proofs by Tamarin with traditional pen-and-paper proofs.
Human errors in security protocols. To formalize and reason about the inherent human limitations and their consequences, we propose the first formal model of human errors in security protocols. By making precise the notion that humans are fallible, the model bridges the gap between formal models of security protocols that fail to consider human errors and the empirical analyses of protocols that demonstrate how these errors can lead to attacks. These considerations are especially important for (democratic) elections, where the results should reflect the will of the human voters. Nevertheless, our observations and the proposed model are not only applicable to voting protocols, but also to other security protocols that involve human users.
Concretely, we define ahuman erroras any deviation of a human from the protocol specification and identify two natural approaches to defining fallible humans. We then single out one of these approaches where we consider fallible humans that can take arbitrary steps instead of following a specification, but may adhere to simpleguidelinessuch as “never reveal your password”. This models non-expert humans and is thus suitable for voting protocols where a lot of users have limited technical experience.
We formalize this approach by further extending the formalism used in the previous contributions. In addition to a distinguished humanH for whom security properties are analyzed, we allow for an arbitrary number of fallible humans in the network. This allows errors made by other humans to affect the security guarantees that hold forH. The resulting formalism for human errors supports automated reasoning by Tamarin and enables the unbounded verification of security protocols involving fallible humans.
To validate our model, we first provide two case studies of authentication protocols, where our formalism automatically finds attacks arising from human errors. In the first case study, we analyze an authentication protocol in detail and compare it with a modified version that uses a heuristic to avoid human errors. In the second case study, we compare existing phone- based authentication protocols that use different methods to authenticate a human to a remote server. We analyze the protocols with respect to
10 1 Introduction different authentication properties and considering humans with different skills, e.g., humans following some guidelines or no guidelines at all. All these protocols successfully authenticate a human agent to a remote server with infallible humans. In contrast, we find numerous and varied attacks when they are analyzed with human errors. Thus, our model allows us to make fine-grained distinctions between protocols with respect to their resilience to human errors. This adds a new dimension to the framework proposed byBonneau et al.[19], where all but one of the protocols have previously been compared.
In contrast to the authentication properties considered in the first two case studies, some security properties state guarantees that depend on actions consciously performed by a human. For example, individual verifia- bility only guarantees that a voter’s ballot is considered in the tally, when the human voter performs specified checks. As fallible humans can behave arbitrarily in our model, it is not straightforward how such properties can be defined and analyzed in the presence of human errors. Therefore, we present an extension of our model of human errors and show how some of these properties’ definitions can be adjusted to analyze them with fallible humans. We illustrate this model extension in a third case study, where we analyze verifiability inAlethea-D’s voting phase with human errors.
1.3 Publications
This work is mainly based on the following publications, where I was the lead author.
1. David Basin, Saša Radomirovi´c, and Lara Schmid,“Modeling Human Errors in Security Protocols”, inCSF, 2016.
2. David Basin, Saša Radomirovi´c, and Lara Schmid,“Alethea: A Provably Secure Random Sample Voting Protocol”, inCSF, 2018.
3. David Basin, Saša Radomirovi´c, and Lara Schmid,“Dispute Resolution in Voting”, inCSF, 2020.
Compared to the original Publication 2, this thesis presents an improved version of theAletheaprotocol with a simpler ballot design. Moreover, the thesis presents a variant ofAlethea, calledAlethea-D, that trades off some of the usability advantages of the original protocol for even better security guarantees. Furthermore, compared to the original Publication 1, an extended model of human errors is presented in this thesis, which allows for the analysis of new properties compared to 1. This extension and other
1.4 Organization and Structure 11 parts of Chapter 5, mainly Sections 5.4 and 5.5, are partially based on the following Master’s Thesis, which I proposed and supervised.
• Andrina Denzler,“Modeling Human Errors in Voting Protocols”, 2019.
1.4 Organization and Structure
In Chapter 2, we present the protocol model that we use throughout the thesis and explain how we formally model protocols, their environments including the system setup and the adversary, and the security properties.
Next, in Chapter 3, we introduce and analyze the random sample voting protocolAlethea. In Chapter 4, we define new dispute resolution properties for a class of voting protocols and analyze under which assumption these properties can be achieved. In Chapter 5, we extend the introduced formal- ism to account for human errors in the analysis of voting protocols as well as other protocols involving human users. We then conclude and present fu- ture work in Chapter 6. Finally, Appendices A–C contain additional details and proofs for the Chapters 3–5, respectively.
Chapter 2
Protocol Model
The three necessary components for reasoning about the security of proto- cols are the protocol, the environment in which the protocol is executed, including the adversary’s capabilities, and the security properties that the protocol should achieve. Given these three things, one can formally reason whether a given protocol satisfies the defined properties in the given envi- ronment. In this chapter, we thus present the formal model which we use to define these components.
As is standard in model-checking, we model protocols and their en- vironment as a (global) transition system. We use a formalism that is general but can directly be interpreted as the input language to the Tamarin tool[79, 94]. This has several advantages. First, Tamarin is a state-of-the art automatic verification tool that enables the unbounded verification of security protocols. Moreover, Tamarin allows to automatically check so calledobservational equivalence properties[8]. We will see that this is needed to model properties that are essential for voting protocols, such as vote privacy. Using this formalism thus allows us to automatically verify many of our claims in the Tamarin tool.
Concretely, our model is based on the Tamarin model[79, 94]with some extensions[10]. These extensions comprise abstractions that ease the specification of communication channels with security properties and trust assumptions, which are now fairly standard in protocol specifications. We next present this model and further extend it with new functions. We will then also extend the model with additional abstractions in the following chapters. In accordance with the three necessary components to analyze protocols, we first present how we specify protocols. Then, we present how we model the environment including the adversary assumptions and the system setup, which specifies how different parties can communicate with each other. Third, we explain how we model security properties and additional assumptions. Finally, we present how our model can be interpreted in terms of a multiset term-rewriting system, which can be used as input to the Tamarin tool.
2.1 Term Algebra and Notation
Our model is based on a term algebra ofmessagesTΣ(X), whereΣ is a signature andX a disjoint, countably infinite set of variables. The ground
14 2 Protocol Model terms areTΣ. Fsym⊂Σdenotes a finite set of function symbols that always contains the functions pair(p1,p2), also denoted by〈p1,p2〉, for pairing of two terms p1 and p2 andfst(p)and snd(p)for the first and second projection of a pairpof terms. Pairing is left-associative and we frequently write〈a,b,c〉for〈〈a,b〉,c〉or omit the brackets〈〉altogether when tupling is clear from the context. Moreover,Fsymcontainsh(m)denoting a (collision resistant) hash function for hashing a termmand function symbols for the standard symmetric and asymmetric encryption. For a messagemand a key k, the functionssenc(m,k)andsdec(m,k)denote the standard symmetric encryption and decryption,aenc(m,k)andadec(m,k)denote the standard asymmetric encryption and decryption, andpk(k)represents the public key (or verification key) associated with a private (or signing) keyk. We use the notation{m}kto denoteaenc(m,k)andsenc(m,k), as it is always clear from the context whetherkis an asymmetric or symmetric key. The standard equational theory for these functions is given in[10, Appendix A] and contains standard equations. For example, pairing and projection obey fst(〈p1,p2〉) =p1andsnd(〈p1,p2〉) =p2and the standard symmetric and asymmetric encryption and decryption obeyadec(aenc(m,pk(k)),k) =m andsdec(senc(m,k),k) =m.
In addition to Fsym,Σcontains the two countably infinite disjoint sets of fresh and public constants, denoted byCfreshandCpub, respectively. Fresh constants model the generation of nonces, whereas public terms represent agent names and other publicly known values. The setsFsym,CfreshandCpub are pairwise disjoint.
2.1.1 Term Algebra Extensions and Additional Notation
We next extend the term algebra with additional function symbols and equations. We will later introduce additional functions and equations, when we only need them locally or when they are easier explained in the context of a chapter.
In addition to Tamarin’s built in standard asymmetric encryption scheme, we model aprobabilisticasymmetric encryption scheme which takes as an additional argument some randomnessr. We will see that explicitly modeling this randomness is required for example when votes are encrypted in voting protocols that should preserve privacy. The encryption of a messagemunder the public keypkand using the randomnessr, is denoted byencp(m,pk,r), also written as{m}rpk, and the decryption of a messagec with a private keykis denoted bydecp(c,k). Moreover, the functions obey the equationdecp({m}pkr(k),k) =m.
2.2 Protocol Specification 15 Also, for a messagemand a keyk, we usesign(m,k)to denotemsigned with the signing keykandver(s,pk)for signature verification, wheresis a signed message andpkthe verification key. We frequently also use{m}kto denotesign(m,k), when the distinction between encryptions and signed messages is clear from the context. The signing and verification functions obey the equation
ver(s,pk) :=
¨m, s={m}k∧pk=pk(k)
⊥, otherwise. (2.1)
stating that when a signature over a messagemis verified with a verification key, then the function returns the signed message m, and otherwise it returns a default value⊥.
Moreover, the functionlistn(x1, . . . ,xn)denotes a list of nmessages and element(l,i) the ith element of a list l. They obey the equations element(listn(x1, . . . ,xn),i) =xifor alli∈ {1, . . . ,n}. Note that if a given protocol requires several lists of different lengths, then such a function and such equations are defined for each (fixed) length. We will use the follow- ing notation for lists. We write[xi]i∈{1,...,n}forlistn(x1, . . . ,xn). Similarly, we write[f(xi,yi)]i∈{1,...,n}for a list whose elements have the same form, but may have different values. When it is clear from context over which values we quantify, we omit the indices. For example, we write[x]and [f(x,y)]for the above lists, respectively. Also, we write[x]iand[f(x,y)]i
for theith element in the lists, i.e., corresponding toelement([x],i)and element([f(x,y)],i). Furthermore, we writeπ[x]to denote the permuta- tion of a list[x]that is defined byπ. Moreover, for two lists[x]and[x0], we denote by[x]⊆l[x0]that the elements of[x]are a sub-multiset of the elements of[x0].
For two message termsm1andm2, we writem2`sm1to denote that m1is a subterm of the composed messagem2. We writex :=y for the assignment of ytox.
2.2 Protocol Specification
A protocol consists of two or morerole specifications, which specify the behavior of the different communicating roles, and possibly of protocol setup assumptions. We model protocols as transition systems that give rise to a trace semantics and present them usingmessage sequence charts(MSCs for short), see for example Figure 2.1. Each role is depicted by a verticallife lineand named by the box on top. For example, the first line in Figure 2.1
16 2 Protocol Model specifies the roleHmodeling a (human) voter. Thus, role specifications are defined by the projection of a message sequence chart to individual life lines and correspond tostrandsin the strand spaces model[100]and processesin the applied pi calculus[3].
A role specification depicts the role’sevents, ordered sequentially. This includes a role’s send and receive events that are depicted by arrows that start at the sender and end at the receiver. The sent messages are spec- ified on top of the arrows. Furthermore, the role specification depicts a role’sinternal computations, depicted by dashed squares. For example, fresh xdenotes that a role generates a fresh random noncex. Finally, a role specification definessignalsby solid squares. A signal is a term with a distinguished top-most function symbol. Signals have no effect on a protocol’s behavior, but serve to label events in executions to facilitate reasoning about the protocol’s security properties. We distinguishexplicit signalsthat are defined in the specification andimplicit signalsthat are recorded during the protocol execution but are not explicitly included in the specification. We will explain signals in more detail when we present the execution model in Section 2.4.
Roles may possess terms in theirinitial knowledge, which is denoted by the explicit signalknows. We require that in a specified roleR, any message sent byRmust either occur inR’s initial knowledge, be freshly generated byR, or be deducible from the messages thatRinitially knows, freshly generated, or received in a previous protocol steps. Deducibility is defined by the equational theory presented above.1 For example, when a roleRreceives a message{m}pk(k)and knows the decryption keyk, thenR can usemin subsequent protocol steps (modeling thatRcan decrypt the message). However, ifRdoes not knowk, it can only use the term{m}pk(k)
that it received as a whole as it cannot decompose it.
During protocol execution, roles are instantiated by agents, i.e., the parties involved in the protocol. By using the same termmin the initial knowledge of multiple roles, we model that agents instantiating these roles share some knowledge at the protocol’s start. In some protocols, multiple agents instantiating the same role all communicate with the same agent instantiating another role. For example, in elections there are thousands of voters which all communicate with the same few authorities. For readability, we show each distinguished role only once in the protocol specification.
We then use the list notation[xi]i∈{1,...,n}in the specification to indicate, for example, that a voting authority expects the same kind of messagex
1We also allow the sending of keywords and message tags, such as‘OK’, even though we do not always explicitly list them in the initial knowledge for readability.
2.2 Protocol Specification 17
H P S BB
knows(H,〈P,v,BB,S〉) knows(P,〈S,pkS〉) knows(S,〈skS,BB〉) knows(BB,〈S〉) v
fresh r
{v}rpkS
If valid, add{v}pkrSto[b]
[v]:= [decp(b,skS)]
[b],[v]
BBrec([b]),BBtal([v]) [v]
verify(H,v∈[v])
Figure 2.1: The protocolSimpleVote, orPrSVfor short, wherepkS=pk(skS). fromnmany voters during execution. As this numbernis usually fixed in the context of a concrete protocol specification, we use the list notation[x] (omitting the indices) most of the time.
Some protocol setups may state additional assumptions with respect to the relation of agents instantiating different roles. For example, whereas for some voting protocols it is allowed that multiple voters use the same platform to cast their ballot, in other protocols it is assumed that each voter uses a different (personal) platform. We assume that assumptions about these relations can be specified as part of the protocol, even though this is not visible in the MSCs. Often, we describe such assumptions together with thesystem setup assumptions, introduced below in Section 2.3.1.
Example1. Figure 2.1 depicts a simple (insecure) voting protocol which we callSimpleVote, orPrSV for short, and which serves as a running example in this chapter to explain our protocol model. The protocol specifies four rolesH,P,S, andBB. These role can, for example, represent the following roles which are typical for voting protocols: a human voter roleH, the voter’s platformPused to cast a ballot over the Internet, the remote voting authority, also called voting server,Sthat collects all ballots and computes
18 2 Protocol Model the election’s result, and a public bulletin boardBB, where all results are published. We assume that each voter uses his personal platformPto cast a ballot.
At the protocol’s start,Pknows the public (encryption) keypkS corre- sponding toS’s private keyskS, which is inS’s initial knowledge. First, a voter enters his votevon the platformP. Then,Pgenerates some random- nessr, indicated byfresh r, and usesrto encrypt the received vote with a probabilistic encryption function under the public key ofS. We call the result of this computation theballot. Pthen sends the ballot toSandS collects all received valid ballots in a list[b]. As explained, even though there are multiple voters, we only show one of them for readability and indicate by the list notation thatSreceives ballots from multiple voters.
Sthen decrypts each of the ballots in the list[b], which results in the list of votes[v], and sends both list toBB. We denote by the explicit signals BBrec([b])andBBtal([v])that the recorded ballots[b]and the votes in the final tally[v]are published on the bulletin board. In the final protocol step,H reads the list of votes fromBBand checks whether the vote that he has previously sent is contained in this list, indicated by the explicit signal
verify. 4
Naming convention for keys. In this thesis, we do not differentiate between a role’s private and signing keys. We usually use the termskX to refer to the roleX’s private (and signing) key andpkX to refer to the corresponding public (and verification) key. A role may possess long term keys that can be used for several executions of the same protocol and short term keys that are generated freshly in each protocol execution. If a role possesses both short term and long term keys and we would like to stress this difference, we uselskXandlpkX to refer to the long term private and public key (or signing and verification key). Moreover, we usekX Y for shared (symmetric) keys that are known to the rolesX andY. We also use superscripts sometimes to further distinguish similar keys.
2.2.1 Human Roles
In may protocols, and especially in voting protocols, we require end-to-end guarantees from ahumanrole to some other role, for example from the human voters to the remote voting server in the protocolSimpleVotefrom Figure 2.1. In reality, humans have limited computational capabilities and need a device to assist them with computations. To realistically model this, we distinguishhuman rolesfrom roles executed by machines and assume

![Figure 3.5: Game IND–SG–out, where [ ps ] is a list of pseudonyms.](https://thumb-eu.123doks.com/thumbv2/1library_info/5343873.1682090/80.629.99.535.101.187/figure-game-ind-sg-ps-list-pseudonyms.webp)